Individuals and organisations are under cyber attack around the globe. In the 2022 edition of The Global Risks Report by the World Economic Forum, cyber attacks were placed among the biggest threats to global economic stability. And it’s not only the large and powerful companies that fall victim to such attacks - as shown in these pages hackers actively target companies of all sizes.
Let’s look in detail at some of the common cyber attacks that hackers use to target individuals and organisations.
Phishing Attacks
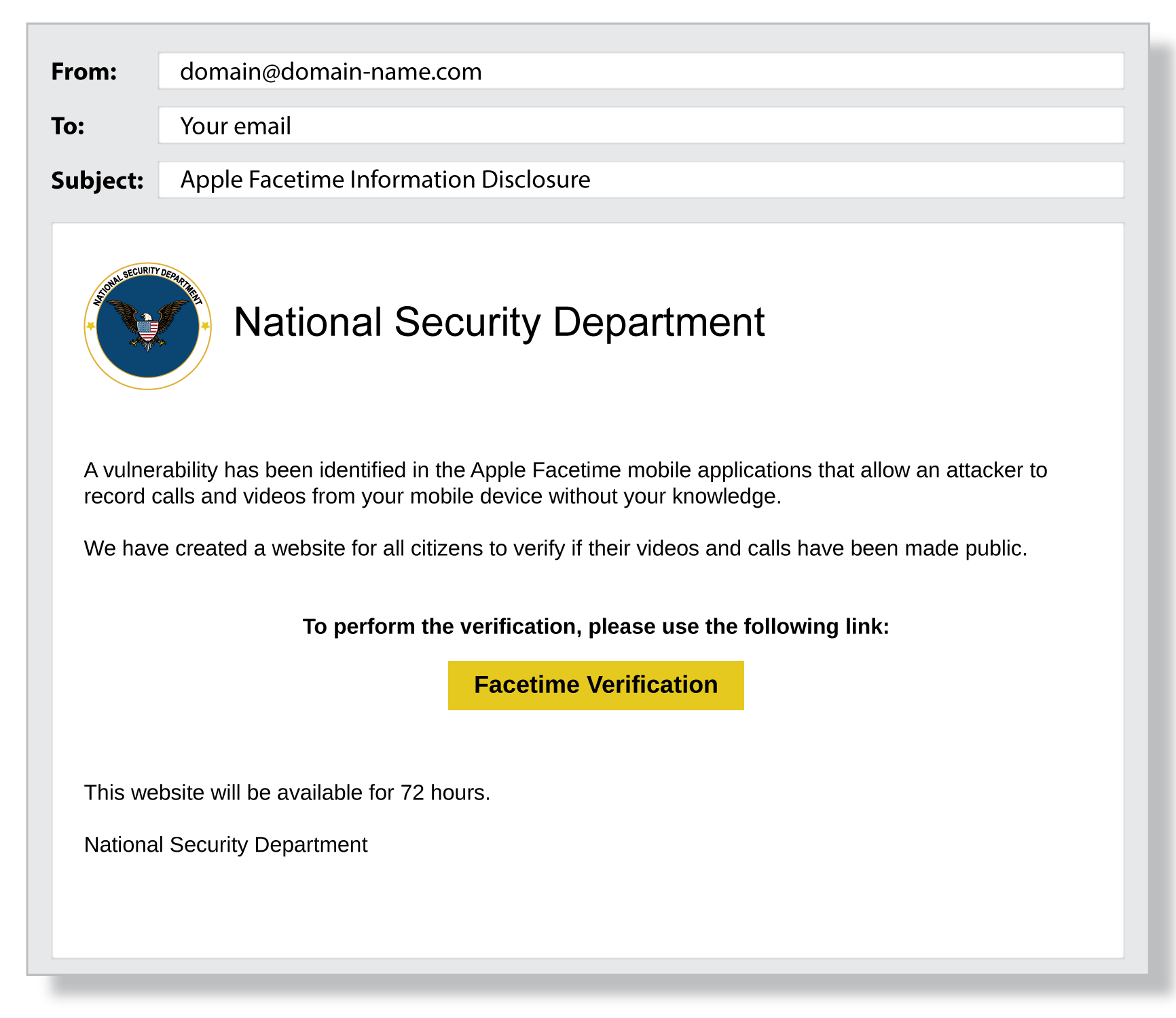
A Phishing attack is a type of cyber attack where the perpetrator sends fraudulent communications through a reputable looking source. The goal is usually to extract sensitive information but this type of attack can also be used as an initial breach in part of a larger cyber attack with the phishing element planting malware (malicious software) that is designed to cause disruption at a later stage. The below image is an example of a phishing email.
Phishing attacks are generally executed through communication channels such as emails and text messages. These emails and messages are often disguised as legitimate communication, but usually contain a malicious link that is disguised. The intention is to make you click on the malicious link to initiate an attack.
Another common trait of phishing attacks is for cyber threat actors to impersonate individuals and brands to project legitimacy. In 2022, 78% of phishing attacks used fake CEO emails to trap employees into divulging sensitive information, according to Trellix (formerly FireEye and McAfee Enterprise).
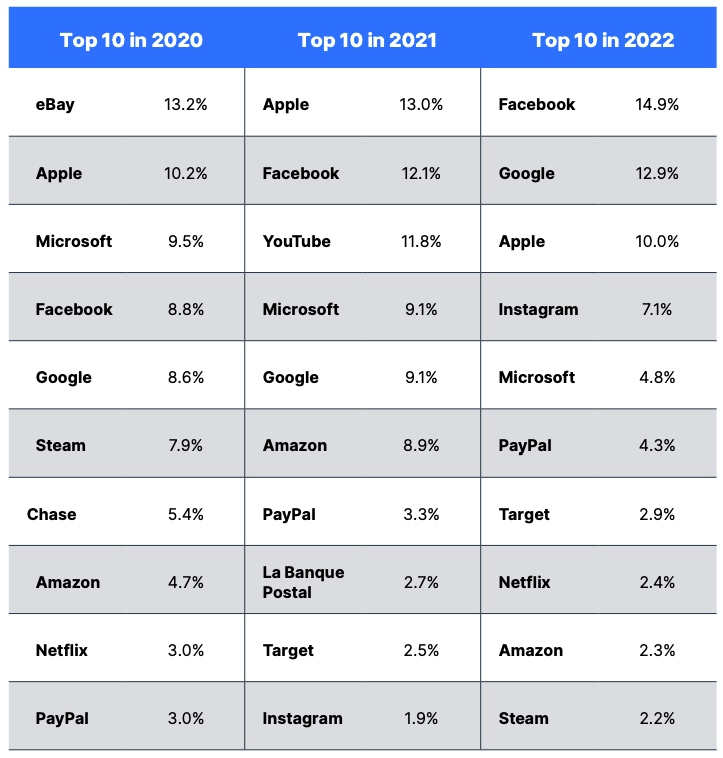
When impersonating brands it’s the big hitters that we’ve all heard of that are used so that they’re easily recognisable. Out of 200 brands tracked last year, Facebook, Google, Apple, Microsoft and Instagram accounted for 49.7% of attacks imitating a brand, according to OpenText - as shown in the image below from their 2023 Cybersecurity Threat Report.
These phishing attacks, using brand names, send out fake customer communications emails such as one from Amazon saying your shipping address is incorrect. The sting comes when you’re directed unwittingly to a malicious website on the pretense of correcting your order details.
How to Prevent Phishing Attacks:
“Very smart people are often tricked by hackers, phishing. I don’t exclude myself from that. It’s about being smarter than a hacker. Not about being smart.”
– Harper Reed, American Entrepreneur & Former Chief Technology Officer to Barack Obama.
Here are a few ways to prevent a phishing attack on your organisation:
- Train your employees to recognise fraudulent communications.
- Implement a zero-trust policy for conveying sensitive information.
- Define a unique communication format across the organisation.
- Cross-verify the source before clicking on any link or divulging information.
- Use anti-phishing tools such as Avanan, Barracuda Sentinel, Cofense PDR, etc.
Malicious Websites
The term ‘malicious website’ is commonly used to describe a website that attempts to install malware on your device. Visiting a malicious website can trigger drive-by downloads, javascript infections, URL injection, and so on. (More on drive-by downloads later).
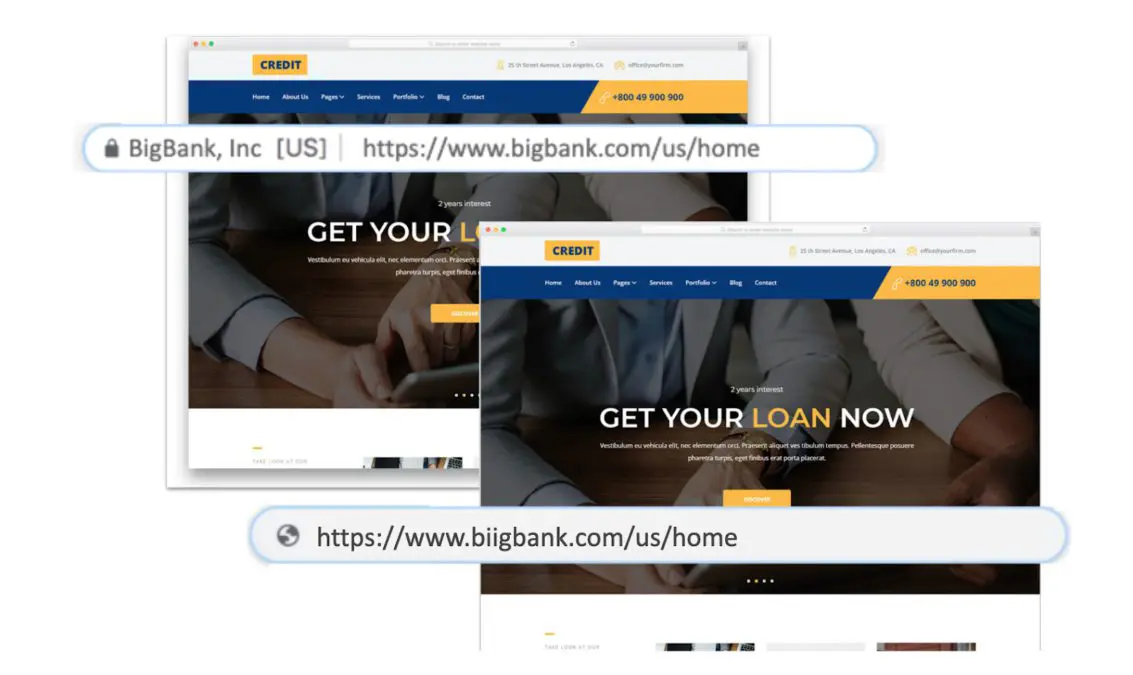
Hackers create fake versions of popular websites to lure their victims. Once you enter these websites, they try to acquire your login credentials or personal information. This can in turn be used to hack personal devices, banking accounts, applications, and more.
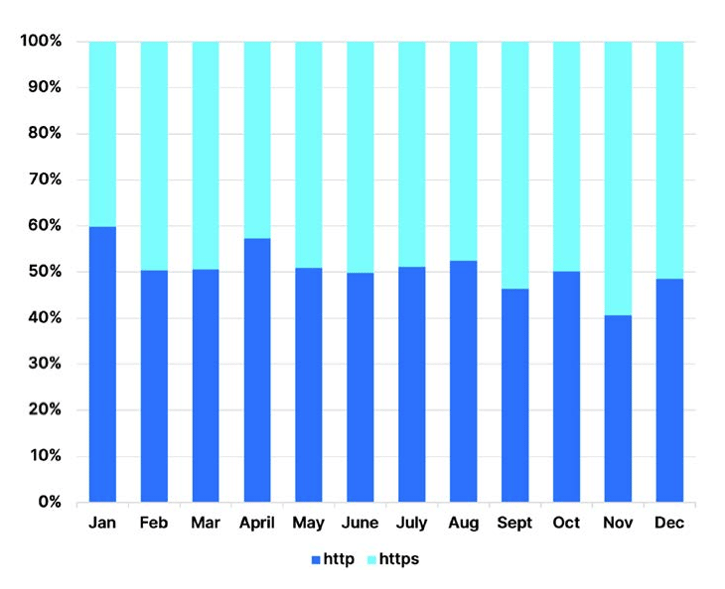
Malicious websites can also take the guise of content and news websites. They can lure their victims with the promise of useful, relevant, or entertaining content. While most people would check if the website is using HTTPS to reliably and securely send and receive data across the internet, this in itself may be a deception. In 2022, on average of those detected, 49.3% of attacks were executed using HTTPS websites, up from 32% in 2021, according to OpenText’s report.
“This marks a 55.5% year-over-year increase. The uptick in phishing sites with HTTPS URLs proves that domain registrars and certificate issuing authorities are becoming less effective at preventing criminals from obtaining these credentials,” it said.
 Hackers also use fake social media sites to collect personal information and credentials. They create fake social media websites that look very similar to the real ones – aside from misspelled versions of the actual website’s URL. The sites can lure targets in with direct messages, following the same pattern as the other phishing attacks, but instead of brands, these attackers impersonate your friends.
Hackers also use fake social media sites to collect personal information and credentials. They create fake social media websites that look very similar to the real ones – aside from misspelled versions of the actual website’s URL. The sites can lure targets in with direct messages, following the same pattern as the other phishing attacks, but instead of brands, these attackers impersonate your friends.
How to Protect Your System from Malicious Websites
Here are a few measures you can take to protect your systems from malicious websites:
- Check the URL in detail before opening the website.
- Use browser security tools such as Microsoft Edge, Norton Safe Search, AVG LinkScanner, etc.
- Use network filtering and firewall protection software such as Cisco Umbrella, WebTitan Cloud, NG Firewall, etc.
Network Scans and Exploitation
Network scans can detect vulnerabilities in a digital infrastructure. It is a part of cybersecurity to discover said vulnerabilities, but as such these scans can also be used by hackers for the same purpose. The difference is intent. Hackers want to exploit the vulnerabilities instead of fixing them.
A hacker will scan through the digital infrastructure of a company to look for vulnerabilities. Hackers will then usually exploit vulnerabilities in communication channels, database access, and open-source software. These vulnerabilities serve as cyber-attack surfaces and entry points for hackers.
The 2023 Open Source Security and Risk Analysis Report by Synopsys highlighted that 84% of code bases (collections of source code used to build a particular software system) have open-source vulnerabilities. With GitHub stating in their 2022 Octoverse report that 90% of companies rely on open source code, such vulnerabilities leave digital infrastructure open to exploitation. A complex digital infrastructure may contain several vulnerabilities in software, cloud, operating systems, servers, communication channels, mobile devices, and so on.
The 2022 State of Attack Surface Management Report from Randori highlights that 69% of data breach attacks can be attributed to vulnerable internet-facing assets. Hackers use such gaps to introduce malware and ransomware into a company’s digital infrastructure, where, once the hackers get access to the data, allows them to encrypt it and demand a ransom. IBM’s Cost of Data Breach Report 2022 states that 83% of organisations fell victim to more than one data breach attack in the previous year.
How to Prevent Network Scan Attacks
“If you put a key under the mat for the cops, a burglar can find it, too. Criminals are using every technology tool at their disposal to hack into people’s accounts. If they know there’s a key hidden somewhere, they won’t stop until they find it.”
– Tim Cook, CEO of Apple.
Here are a few ways to prevent network scan attacks on your IT infrastructure:
- Conduct periodic vulnerability analysis.
- Identify and fix the vulnerabilities before the hackers find them.
- Implement zero trust policy for access control.
- Use intrusion detection system (IDS) and intrusion prevention system (IPS) such as Cisco NGIPS, Trellix Endpoint Detection and Response (EDR), etc.
- Assess whether cloud security posture management tools might help you identify risks in your cloud infrastructure.
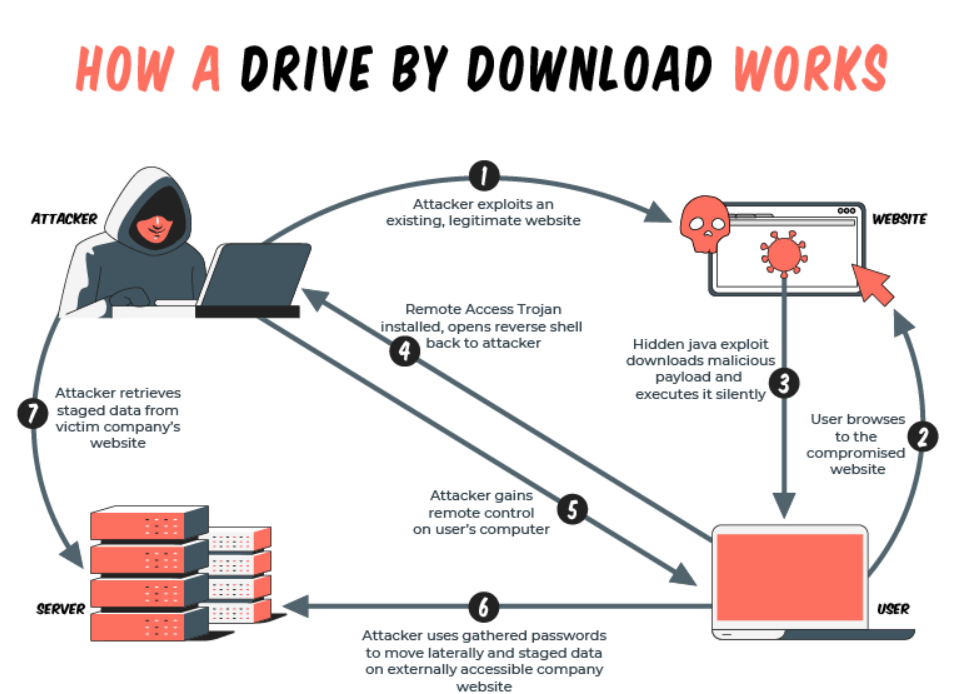
Drive-by Downloads
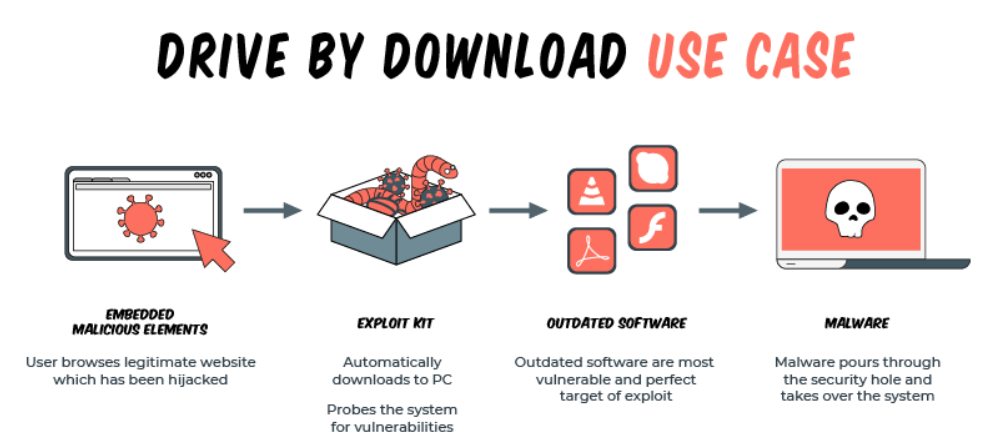
A drive-by download is a download that is automatically triggered without the user’s permission. The downloaded item can be an unwanted program/application or malware.
Hackers can attack a website and implant malicious code there. Once this code is installed, it can infect all those who visit the website. These scripts are automatically downloaded onto the device to execute spyware, malware, or ransomware.
This type of attack can be used by hackers to target a specific group of people or an organisation. The hackers would identify websites commonly used by those they wish to target. They then find vulnerabilities to exploit, in the often visited website, and implant a script on it. When the targets visit that website, it executes the drive-by download script automatically. These programs are installed on the user’s device without their consent.
Hackers can also use phishing attacks through emails or social media messages to bait targets to open a compromised website. They can also target intended downloads and attach malicious applications as hidden payloads.
Once they are on your device, these programs can do a lot of damage executing encryption, installing spyware, extracting data, infecting other devices, and more.
How to Prevent Drive-by Downloads
Here are a few ways to prevent drive-by download attacks on your or your organisation’s systems:
- Use tools for browser security, network filtering, and firewall protection.
- Keep cybersecurity software updated.
- Do not allow autodownloads to any website.
- Do not use unlicensed software and applications.
- Allow anit-virus and anti-malware software to scan all downloads.
- Conduct periodic scans to identify malware in your system.
Wi-Fi Attacks
A Wi-Fi attack targets wireless system information and wireless networks. This type of cyber attack hits the Wi-Fi network to compromise the network itself or the devices connected to it.
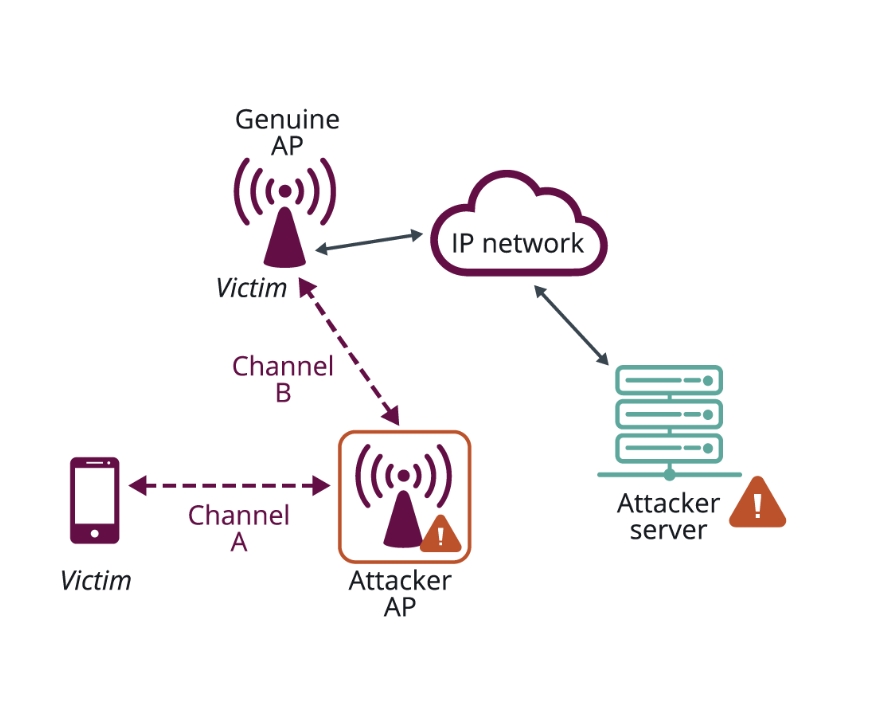 Hackers can attack a company’s Wi-Fi network using several methods such as Sniffing, Spoofing, Wardriving, and Encryption Cracking. These methods exploit the vulnerabilities in hardware, software, encryption, and accessibility to conduct attacks.
Hackers can attack a company’s Wi-Fi network using several methods such as Sniffing, Spoofing, Wardriving, and Encryption Cracking. These methods exploit the vulnerabilities in hardware, software, encryption, and accessibility to conduct attacks.
Through these attacks, hackers can intercept the data transmitted between a device and a router. If the company’s Wi-Fi network gets compromised, hackers can access data from all the devices connected to that network.
Hackers can also use a proxy Wi-Fi network that has the same Service Set Identifier (SSID) as the actual router. Most devices automatically connect to previously connected Wi-Fi networks and hackers exploit these features using a stronger proxy network. Once the devices are connected to the fake network, hackers can access all traffic that passes through the router.
Although most of the data transmitted through Wi-Fi networks is encrypted, hackers can use a variety of brute-force software to decrypt the data. They can also run similar programs to directly attack a Wi-Fi router to gain a decryption key or access passwords. They can then exploit all the devices connected to the Wi-Fi network.
How to Prevent Wi-Fi Attacks on Your System:
“We discovered in our research that insider threats are not viewed as seriously as external threats, like a cyberattack. But when companies had an insider threat, in general, they were much more costly than external incidents.”
– Dr. Larry Ponemon, Founder and Chairman of the Ponemon Institute
Here are a few ways to prevent Wi-Fi attacks on your company’s network and devices:
- Use strong admin credentials for the router and keep changing it periodically.
- Ensure your Wi-Fi network has a strong encryption.
- Update the router software regularly.
- Do not broadcast your organisation’s Wi-Fi network as a Service Set Identifier (SSID).
- Control the Wi-Fi range to the office’s area.
- Enable MAC filtering to identify and control the devices connected to the network.
Conclusion
Hackers attack both digital infrastructure and individuals to successfully enter or compromise a system. Phishing and Malicious Website attacks target individuals to enter a system. Here they exploit common human behaviour to execute these attacks. Due to this it is an operational imperative for organisations to educate and train their employees about such attacks.
On the other hand, hackers can also exploit vulnerabilities in the digital infrastructure through hardware, software, and networks to execute their attacks. Companies are often unaware of such vulnerabilities in their infrastructure. If that's you, in 2023, you first need to conduct a vulnerability assessment to identify the problem areas and then execute appropriate cybersecurity measures to reinforce your infrastructure. Or else.