If you’ve just clicked on a phishing link, you’re probably starting to worry. Have you just unleashed dangerous malware onto your systems? Is a hacker now scanning through all your files in a plot to steal your identity?
Before you tear your hair out speculating, read this article, we’ll tell you exactly what to do to prevent any damage and how to avoid clicking on phishing links in the future.
What is phishing?
First, a quick recap. You probably know that phishing, in general terms, is a social engineering tactic used by hackers to lure unsuspecting victims into handing over their personal information.
This data is precious to hackers, who might sell it on the Dark Web or use it to access other accounts owned by the user to gather more information or launch an even broader phishing campaign.

Phishing has evolved over time and can now be highly sophisticated. We are currently dealing with different kinds of phishing - URL phishing, Clone phishing, business email compromise - and different entry points.
People can get tricked via the traditional email method, but we’re now seeing phishing attacks made over the phone (vishing) or SMS (smishing) become more popular among hackers. In fact, it was reported that SMS-based scams rose by 328% in 2020 during the pandemic.
So, don’t be too hard on yourself for clicking on a phishing link. People are fooled every day as these scams become harder to spot. According to the UK Government’s Cyber Breaches survey, phishing took first place as the most common threat vector this year, making up 83% of cyber attacks.
How do you know if you’ve been phished?
Ok, so maybe you didn’t click on a phishing link…or perhaps you did? If they’ve done their job well, hackers won’t make it glaringly obvious that they’re trying to fool you. Luckily, most phishing attacks usually have one or two giveaways.
The sender: If the message appears to be from someone you know, check in with them and ask if it was really them who sent it. They’ll probably appreciate the heads-up if it turns out someone has breached their account!
You should also check the sender’s domain closely to see if it’s consistent with who they say they are. Often hackers will change just one letter of a trusted domain, which the recipient might easily miss.
The content: Read through the message. If you’re being urged to act fast or provide specific information like banking details, treat it with caution.
The spelling: Phishing emails are often not written in the best English, so look out for poor spelling and grammar, which might suggest it’s spam.
The link: Hover over the link itself to see if it’s consistent with the domain.

Damage control
If, after a bit of digging, you’re convinced you’ve been fooled by a phishing attack, it’s time to do a bit of damage control.
Don’t provide any personal information: If the link has taken you to a page asking you to fill in your details, avoid this at all costs. This gives the hacker precisely what he’s after.
Disconnect from the internet: Clicking on the link may have triggered malware to be downloaded, so it’s a good idea to disconnect from whatever WiFi you’re using to avoid malware moving across the network onto other devices.
Back up: Ideally, you back up regularly anyway, so this doesn’t necessarily have to be a complete device backup, but if malware has been downloaded onto your device, chances are it could wipe or damage your data.
Backing up important data can be done using an external hard drive or USB and will prevent you from losing everything in the case of a data breach.
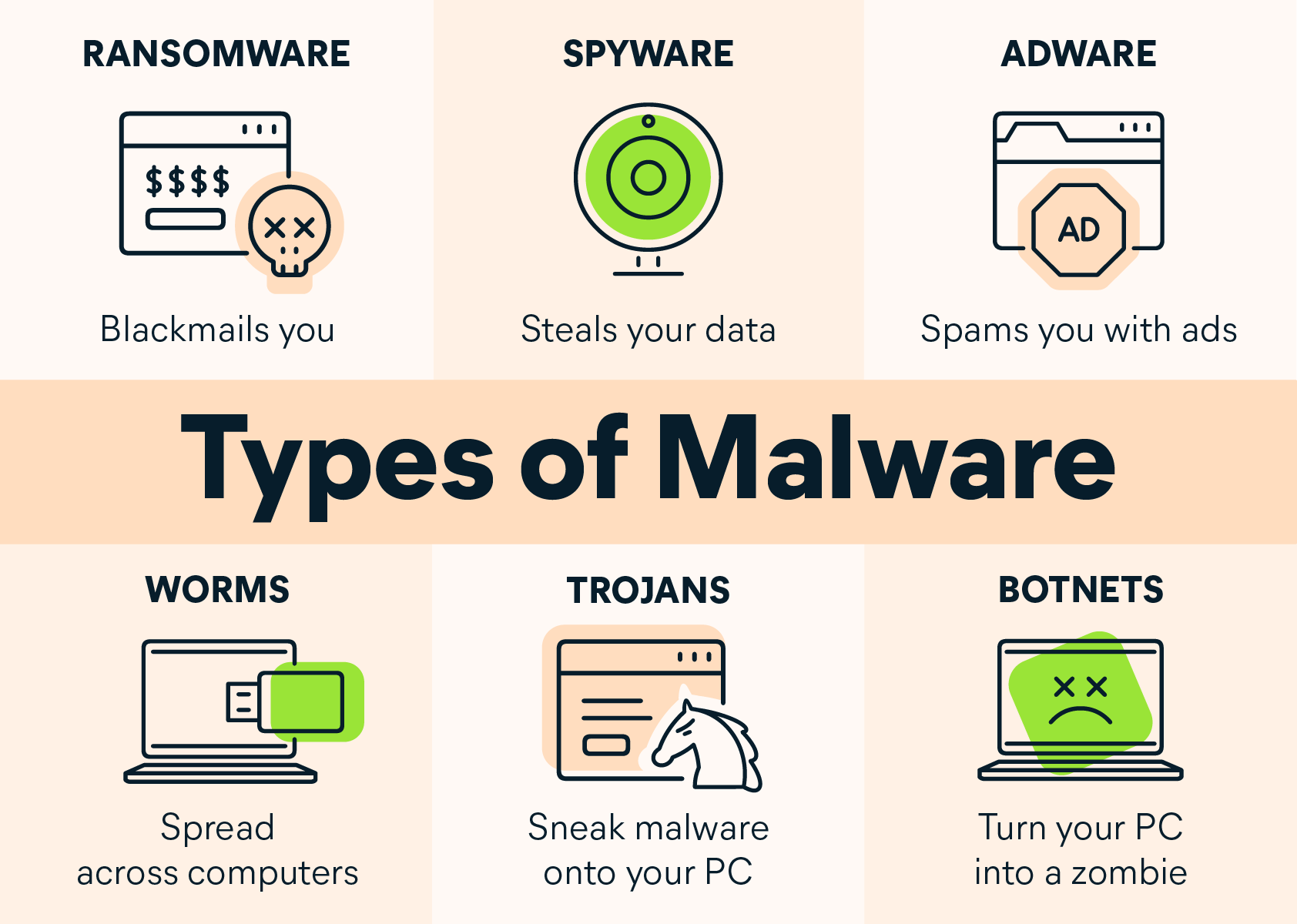
Check for malware: Whether you suspect malware or not, it’s always best practice to scan your system for viruses that might have been downloaded when you clicked on the phishing link. Most operating systems already have built-in antivirus software, which you can use to check if any harm has been done.
If you don’t have any malware scanning software, there are plenty of free and paid options online, but you should use another device to download the software online and then, with a USB, transfer it across to the affected device. You mustn’t reconnect the original device to the internet to avoid any malware spreading.
Change Passwords: Hackers can access your credentials via phishing links, so if you think you clicked on one, changing your online passwords, particularly to things like bank accounts, is essential to avoid further damage. Don’t reuse the same passwords across accounts, as this makes it even easier for a hacker to wreak havoc. Always create strong, unique passwords, and use something secure like a password manager to keep track of them.
Better safe than sorry
You might escape from clicking on a phishing link with no real damage done. Nevertheless, use it as a wake-up call to help you act more cautiously online in the future.
It’s always best to assume the worst and go through the steps above if you think you’ve been targeted in a phishing, vishing or smishing attack.
Remind yourself periodically of what to look for when you’re being phished, especially as attacking techniques grow more sophisticated.
If you’re ever uncertain whether your data has been stolen, you can quickly check if your domain has been breached with our free online tool.


