Are you thinking about Cyber Essentials for your business? Wondering what it involves? Maybe you just want to have a look at the requirements and see how many your business already meets?
First of all, for any newbies here, let's break down what Cyber Essentials actually is.
Feel free to skip this part if you're ready for the nitty-gritty.
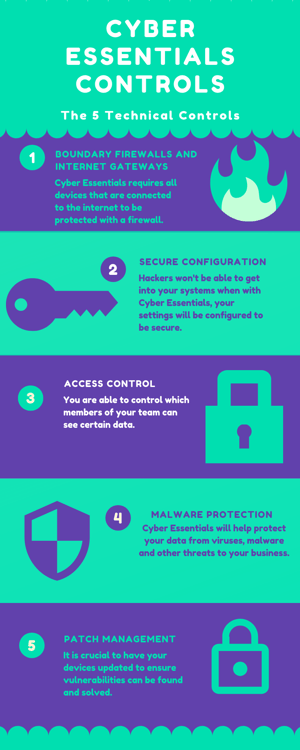
Cyber Essentials is a government-operated cyber security scheme that offers businesses a framework to help significantly reduce their risk against common internet-based attacks. Developed by the National Cyber Security Centre, Cyber Essentials incorporates 5 fundamental technical controls that, if implemented, can reduce your risk by up to 80%.
Nowadays, the NCSC has a single delivery partner for the scheme - The Information Assurance for Small and Medium Enterprises Consortium (IASME). IASME works with a number of Certification Bodies across the UK like Cyber Tec Security, all of whom have the ability to certify businesses to the standard.
Two levels of certification...
Your Cyber Essentials journey starts out by achieving the Basic certification and is fully complete when you've secured the Plus certificate.
What's the difference?
Well, at the Basic level, you're just filling out a questionnaire relating to the security processes, policies and controls you have within your business, but nothing is actually verified. You can still fail if your answers are not in line with what the standard requires, but even if they are, no one actually tests your devices and systems to confirm.
The Plus assessment, however, requires an official auditor to actually scan your infrastructure in order to determine whether or not you are complying with the standard.
Essentially, this is why we always recommend achieving Cyber Essentials Plus, because it's properly verified and therefore a true testament to how secure your organisation really is.
It's also worth noting here that you do need to complete Plus within 90 days of completing your Basic in order for the certification to be valid. At Cyber Tec, we help you prepare for Plus while you're doing your Basic so there's no danger of surpassing this deadline.
Still with me?
Let's dive into the technical requirements...
As of January 2022, there have been some updates that can make the assessment more challenging so it's more important than ever that you have a good understanding of what is expected from you in order to comply with the standard.
Cyber Essentials Plus Checklist
Now, we won't go through every question (there are a fair few!), rather this will focus on the questions that are most important or that many find particularly difficult. You'll be able to download the full question set provided by IASME at the bottom of this page -> skip there now if you'd like!
The first few sections are there to gather information about your company and determine the scope of the assessment. Be prepared to provide information about devices, servers and networks that will be included in the scope of the assessment. You'll also need to list any cloud services used by your organisation.
Cyber Essentials grants free insurance to companies with a turnover of less than £20million so details relating to this will need to be collected at the start of the questionnaire but does not affect your assessment result.
Office Firewalls and Internet Gateways
- When corporate or user-owned devices (BYOD) are not connected to the organisation’s internal network, how are the firewall controls applied?
This question was introduced in the 2022 standard and seeks to establish what method you have of enforcing firewall controls on devices outside of the network you control, for example, devices may be connected to Azure AD and receive policy settings through this.
- Describe the process for changing the firewall password
You have to show you are aware of this process. Explain how the password was configured and where it can be managed. The question preceding will also ask you to confirm that you change all default passwords for new routers and firewalls.
Other requirements relating to firewalls include:
- Firewalls should block all services from inside the network from being accessed from the internet
- Password must either: use MFA and be a minimum of 8 characters, use automatic blocking of passwords and be a minimum of 8 characters, OR be a minimum length of 12 characters
Secure Configuration
- Have you removed or disabled all the software that you do not use on your laptops, desktop computers, thin clients, servers, tablets, mobile phones and cloud services?
You have to make sure that all applications and services that aren't used are not active. Some companies may utilise solutions like Endpoint Manager and AppGuard to limit users from installing and changing software so only known and legitimate software is being used.
- Do you run external services e.g. hosted on a VPN server, a mail server, or an internet application, that provides access to confidential data to users across the internet?
If yes, you'll need to state again which password method you use (listed above) to keep these processes secure.
- Do you have a password policy to guide users?
Your password policy should offer guidance on creating strong unique passwords and how to store them, and be easily accessible to employees.
- When a device requires a user to be present, do you set up a locking mechanism on your devices to access the software and services installed?
Where a device requires the physical presence of a user to gain access to the user has to unlock the device using biometrics, a password or PIN.
Patching Management
This is a crucial section of the Cyber Essentials assessment, and one where a lot of companies can fail, so take note!
Be prepared to list your Internet browsers, email and office applications so it can be verified whether or not they are in support. You'll also be asked about your malware protection - note that all MAC devices will need 3rd party anti-virus protection.
- Are all high-risk or critical security updates for operating systems and firmware installed within 14 days of release? Are all high-risk or critical security updates for applications (including any associated files and any plugins such as Java, Adobe Reader and .Net.) installed within 14 days of release?
Under the current standard (2022), this now includes any and all security updates with a CVSS score of over 7.0. This will actually be tested for the Plus assessment and can catch a lot of people out. It's strongly recommended that any browsers not in use are removed as often these won't update unless actually opened and used.
- Are all updates applied for applications and operating systems by enabling auto-updates?
Ideally, this should be a 'yes', but you may or your MSP may be using something else for patch management.
- Have you removed any software on your devices that is no longer supported and no longer receives updates for security problems?
Any and all software no longer supported by the developer (i.e. end-of-life) must be removed because they will no longer be receiving security updates. If you do have any, from 2023 you'll have to prove that it has been placed on its own sub-set, prevented from inbound and outbound internet access.
User Access Control
- Are all user and administrative accounts accessed by entering a unique username and password?
Often companies will have shared admin accounts, particularly if they outsource IT support, but this is not compliant with Cyber Essentials. IT providers should have unique accounts per engineer, not a shared account on your system.
You'll need to answer questions relating to your management of administrative accounts, including:
- Process for granting admin access
- Process for ensuring admin accounts are only used for administrative activities (admin accounts should never be used for standard user activities like web browsing)
- Process for tracking and reviewing admin accounts in your organisation
- Which technical controls are used to manage the quality of your passwords within your organisation?
This question asks you to outline your methods of ensuring strong, healthy passwords. This might include:
- All user accounts require the user to authenticate
- Protection against Brute-Force In Place (MFA / Throttling / Locking Out)
- Quality of Password Controls (MFA, Min length 12 characters, Min 8 with common block)
- Support for Good Password Choice (Education/Policy/Password Managers/ No regular changing)
- There is a process to handle any breached password and change of it
With the 2022 updates, many of the questions in this section of the assessment now include cloud services. Wherever your cloud services support Multi-Factor Authentication, it must be enabled. Password quality control will also refer to any cloud accounts.
Malware Protection
- Are all desktop computers, laptops, tablets and mobile phones protected from malware by either: anti-malware software installed, limiting installation of applications to an approved set, or application sandboxing?
For most, the first two will apply here. Sandboxing is rare. Don't forget MACs must have fully working 3rd party anti-virus.
- Where you have anti-malware software installed, is it set to update daily and scan files automatically upon access?
Anti-virus will usually update by default but this will be checked in the Plus assessment so make sure this is the case!
Other requirements relating to malware protection:
- You should have a list of approved applications and only these should be installed (including on BYOD devices)
- Your anti-virus should have a plugin to protect your system from malicious websites.
While this Cyber Essentials checklist has not been exhaustive, it should give you a good idea of what's covered and where it's important not to go wrong. The scheme is going to continue to update in line with our evolving security landscape so it is always advisable to take advantage of guided options when going through the assessment. IASME auditors are highly knowledgeable about the standard's requirements and can save you a lot of extra hassle by offering their direct counsel throughout the assessment process.
At Cyber Tec Security, we also provide a Pre-Assessment scanning process with the Cyber Essentials Plus certification, so you can get all your systems checked and verified to the standard before officially completing the final assessment. With some of the new technical changes, especially relating to patch management, it can be very easy to fail Cyber Essentials Plus without proper preparation.
Find out more about achieving Cyber Essentials Plus with an Assured Pass here.
To review the full question set for Cyber Essentials, as produced by IASME, you may download this below. If you have any questions, feel free to contact us and one of our friendly assessors will be happy to help.


