In today’s business world, it is almost a certainty that your organisation is relying on external suppliers to help deliver products, systems and services.
Supply chains are crucial to businesses but while this brings many benefits and conveniences to the way major companies operate, it usually means external supplier personnel will need to access your business’ systems and data. This immediately becomes a security problem if it’s not handled in the right way.
As supply chains grow in size and complexity, it becomes very difficult to manage security at every level and ensure that all your suppliers are secure enough.
Vulnerabilities can surface at any point in the supply chain, threatening your organisation’s security. Cybercriminals know that badly secured third-party suppliers can open a good backdoor to sensitive data and systems, and will exploit these vulnerabilities at the first opportunity.

“A vulnerable supply chain can cause damage and disruption.”
Common Supply Chain Attacks
-
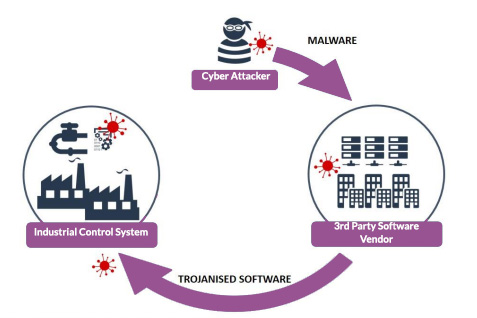
Third-Party Software Providers
Compromising software at the source via suppliers. Malware can be injected into update files which are then installed by the company and infection spreads to other IT systems and software users within the internal network -
Website & Apps
Hackers can add malicious code to apps in development before they’re installed or target core scripts of website builders so users are redirected from the legitimate site to the hacker’s malicious one.
-
Third party data stores
Outsourcing sensitive data and allowing other companies to access it could result in it falling into the wrong hands. Stolen credentials may then be used to gain access to the network.

In 2020, hackers targeted a cyber security company called SolarWinds, specifically a software update that would be installed by around 18,000 customers. They were able to embed malicious code in the update which was innocently installed by government agencies and significant companies like Microsoft and security firm, FireEye. According to Microsoft the SolarWinds attack was the "largest and most sophisticated attack the world has ever seen".
The Risk is Rising...
Supply Chain attacks are nothing new, but they are on the rise. These attacks are popular because they provide the opportunity for hackers to access information from multiple organisations’ through a single third-party supplier. Impressive gains for minimal effort.
The COVID-19 pandemic has also played a part in this rise, spurring a huge drive for the digitization of companies and the way they operate, including working with those in their supply chain.
Businesses have also had to deal with higher demand and restricted supply routes. This rapid diversification only increases the chance for security to be overlooked while cybercriminals wait patiently in the wings to exploit weaknesses.
💡DID YOU KNOW?
In February 2021, a security researcher discovered a new kind of software supply chain attack that would allow access to the internal systems of companies like Apple, Netflix, Tesla and Uber...
“Attackers will always try to find the weakest link, and if a product is downloaded by millions of users it is an attractive target for them. Companies need to increase their attention and investment in keeping the supply chain secure.” [AVAST]
The Time to Act is Now.
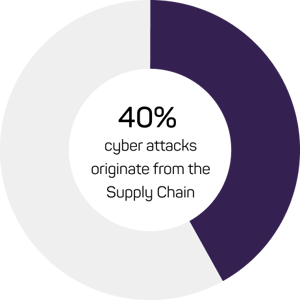
The UK Government’s 2020 Cyber Breaches report discovered that many businesses have never even discussed supply chain risks. This is shocking considering 40% of cyber attacks are now thought to originate from the supply chain.
Incidents like the SolarWinds attack indicate how serious the security risks in supply chains are.
Get in touch with us today to find out how you can protect your supply chain against these risks: contact@cybertecsecurity.com