A stolen password can do a lot of damage.
With access to your accounts, hackers could obtain your full name, address, phone number, and other personal information. That’s everything they need to commit identity fraud.
If they get into your financial accounts, it can be much worse.
So how do hackers steal passwords, and what can you do to protect yourself?
That’s what we’re going to reveal in this guide.
You’ll learn the techniques hackers use to capitalise on security weaknesses and what you can do to stop them in their tracks.
1. Phishing Attacks
Phishing is a deceptive social engineering technique used by cybercriminals. The aim is to trick individuals into revealing their passwords and sensitive information.
The hacker poses as a reputable company and sends convincing emails telling the recipient they need to take action. Some phishing schemes go as far as to create content and fake websites that resemble the real ones.
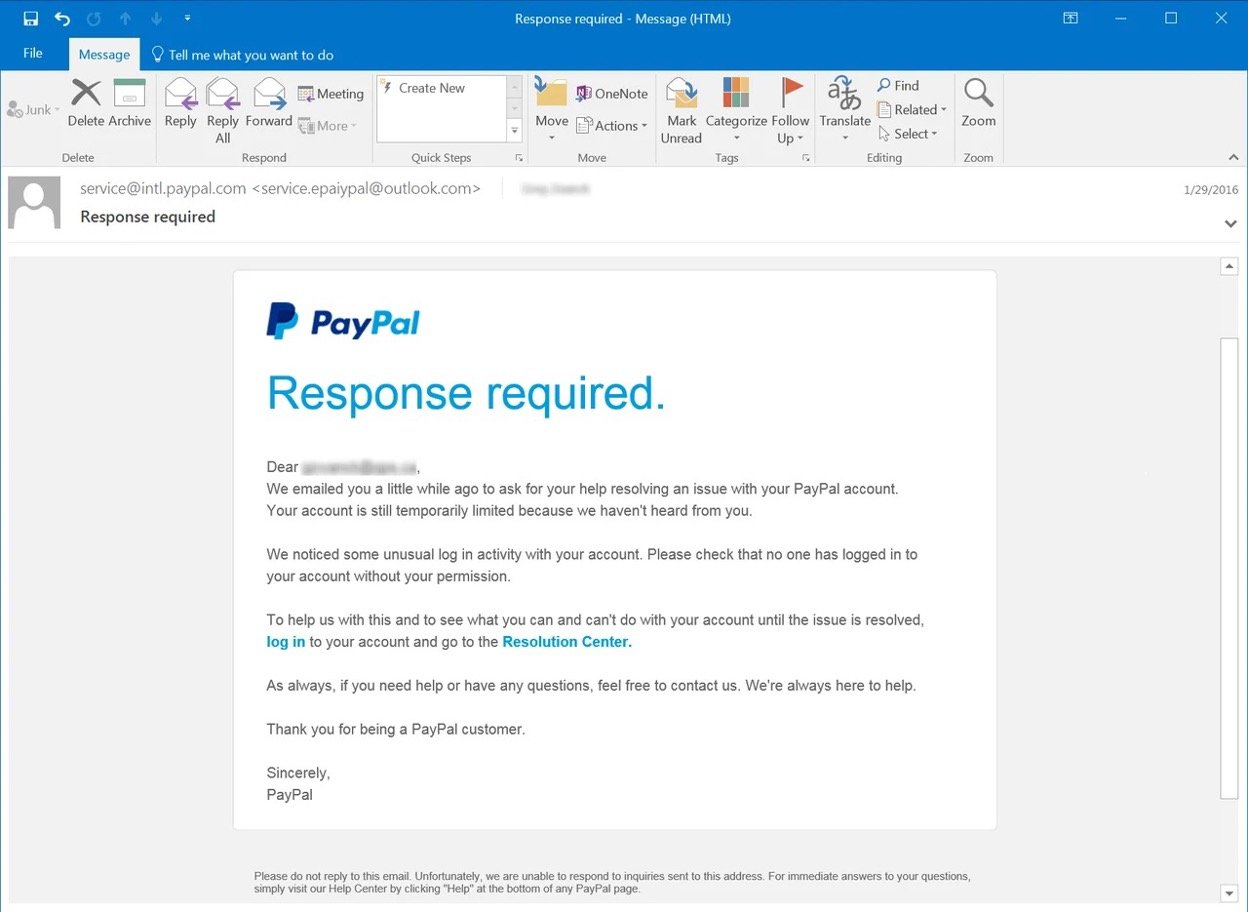
The hacker typically uses fear tactics or enticing offers to prompt users to click on malicious links or enter their login credentials.
Once the victim provides their information, the hackers gain access to their accounts.
How to Protect Against Phishing Attacks
Vigilance and skepticism are your best weapons to combat phishing attempts. Always be wary when you receive unexpected or suspicious emails.
Double-check the sender’s email address and scrutinise the content for any signs of phishing attempts. Legitimate companies rarely ask for sensitive information through email. Be cautious about providing any details without verification.
2. Brute Force Attacks
Brute force attacks are basically a trial and error method by hackers to crack passwords. They use powerful computing tools to systematically try countless combinations until they find the correct one. It’s a guessing game at scale.
Weak and common passwords can quickly be broken in a brute-force attack.
The eCommerce giant Alibaba was the victim of a brute force attack in 2016. Over two months, hackers accessed the passwords and usernames of 20.6 million accounts.
How to Protect Against Brute Force Attacks
Creating strong and complex passwords is the best defence against brute force attacks.
Use a mix of uppercase and lowercase letters, numbers, and special characters. This significantly increases the complexity of passwords, making them harder to crack.
If you run a platform or website, you can implement account lockouts after several unsuccessful login attempts. This limits the number of attempts a brute force attacker can make at guessing a password.
3. Keylogging
Keyloggers are invasive tools hackers use to record every keystroke a user makes. They are usually distributed through malicious software or disguised as hardware devices. This can make them difficult to detect.
Once installed, keyloggers record passwords and other valuable information. Hackers then retrieve this data to gain unauthorised access to accounts and compromise personal data.
In 2019, IBM X-Force researchers identified a surge in the use of HawkEye Reborn v8.0 and v9.0 keylogging malware. Hackers targeted Spanish bank customers with deceptive emails containing the keylogger.
How to Protect Against Keylogging
The first step is being cautious when downloading software. Stick to official app stores and reputable websites. Prevention is always better than cure.
Your secondary line of defence is reliable antivirus and anti-malware software. Good security software can detect and block keyloggers and other malicious programs. Regularly updating and scanning your system can help detect and remove these hidden threats.
4. Credential Stuffing
Credential stuffing takes advantage of users that reuse the same passwords across multiple accounts.
Hackers get hold of username-password pairs from previous data breaches and test them on various platforms. Unfortunately, many people use the same passwords across many accounts.
Hackers can access multiple accounts using the same stolen credentials if one account is compromised.
Uber was the victim of a credential stuffing attack in 2016. Hackers used the exposed credentials of an Uber employee to access their GitHub account. From this account, the hackers found the login details for Uber’s Amazon Web Service S3 buckets. The personal information of 57 million drivers and riders was stolen.
The ride-hailing app was fined $1.2 million by UK and Netherlands regulators.
How to Protect Against Credential Stuffing
The key to thwarting credential stuffing attacks is good password management. Create unique passwords for each of your accounts. That way, a single breach doesn’t compromise all your other accounts.
Multi-factor authentication (MFA) can add an extra layer of security. It makes it more challenging for hackers to gain unauthorised access even with stolen passwords.
5. Malware and Spyware
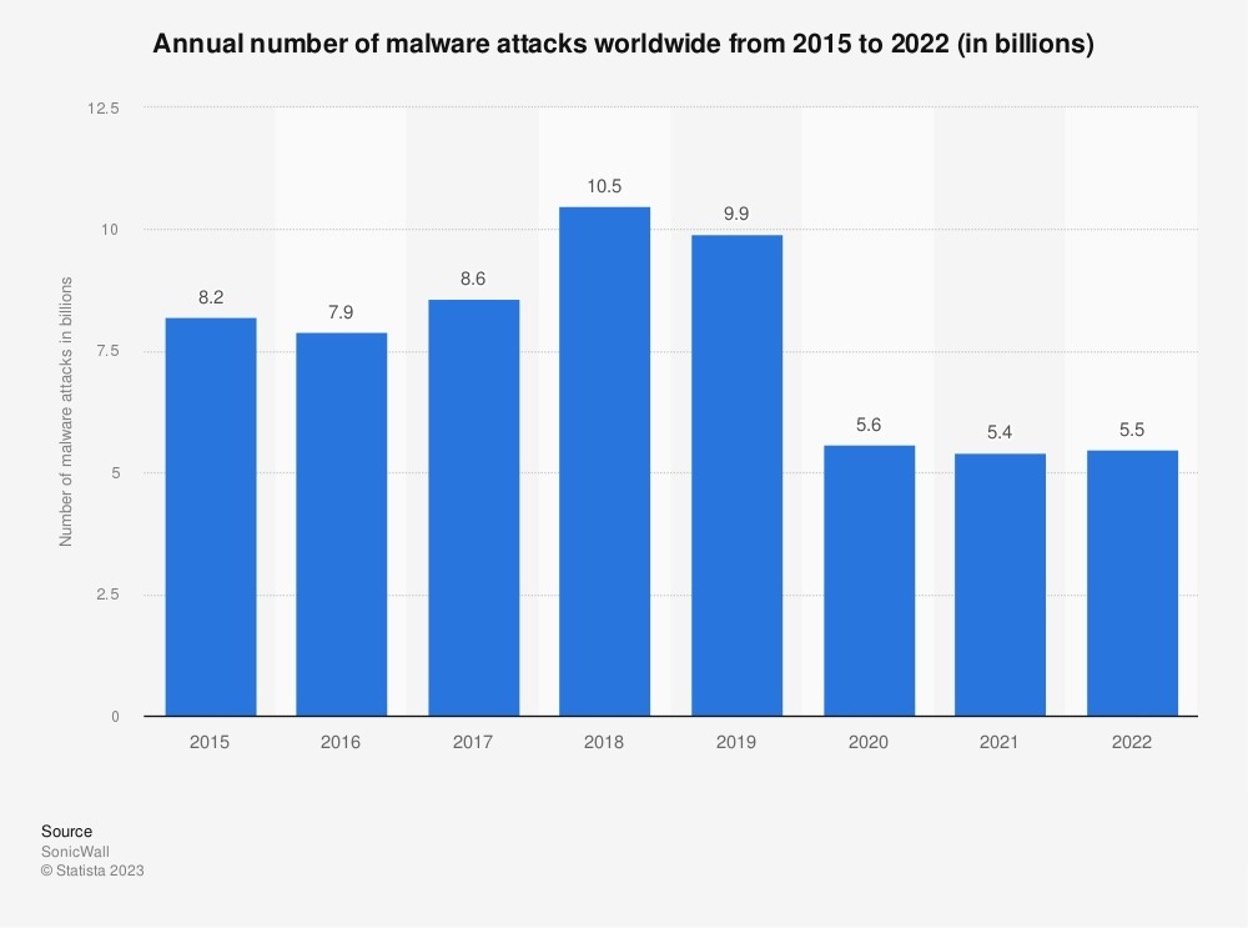
Malware and spyware are malicious programs. They are designed to infiltrate systems and steal sensitive information, like passwords. There are billions of malware attacks every year as shown in the below graph from Statista:
Different types of malware and spyware exist, including Trojans, ransomware, and keyloggers.
We’ve already discussed keyloggers, so what about the trojans and ransomware?
Trojans are disguised as legitimate software or files. Once downloaded and activated, they infect your system.
Ransomware has been all over the news in recent years. Hackers use these programs to encrypt files and demand payment from victims to regain access to their data.
How to Protect Against Malware and Spyware
The best way to protect yourself is to be careful where you download programs. You should also be wary of clicking any links from unknown sources.
Using antivirus and anti-malware software is also essential. These cyber security tools scan for and remove malicious programs. They can prevent trojans and ransomware from causing harm to your system and data.
6. Man-in-the-Middle Attacks
Man-in-the-middle (MitM) attacks exploit unsecured connections between users and websites or applications. Hackers intercept and capture sensitive data, including passwords.
If a user communicates with a website over an unencrypted connection, it’s like sending a postcard that anyone along the way can read. Hackers capitalise on this vulnerability to steal login credentials and other private information.
In 2017, Equifax withdrew its apps after discovering they were vulnerable to MItM attacks.
How to Protect Against Man in the Middle Attacks
When accessing a website, look for the padlock icon in the address bar to check for a valid SSL certificate. You should avoid accessing websites that display certificate errors or warnings.
Public Wi-Fi is more vulnerable to MitM attacks. If you have no option other than public Wi-Fi, consider using a Virtual Private Network (VPN) to encrypt your internet traffic. This can provide an extra layer of security and make it difficult for hackers to intercept sensitive data.
7. Data Breaches and Password Dumps
Data breaches are catastrophic events that expose vast amounts of sensitive data. Hackers gain access to databases or servers and steal user information. This data is then sold or shared on the dark web.
Other hackers use this information to try logging into other platforms where users may have reused the same credentials. With the prevalence of password reuse, this technique often proves successful.
In 2021, hackers dumped a massive 3.2 billion Gmail, Hotmail, Netflix, and LinkedIn usernames and passwords on the dark web.
How to Protect Against Data Breaches and Password Dumps
You cannot do much to stop hackers from infiltrating a third-party website and stealing your login details. Your best defence is to use unique passwords for each account.
You can also use cyber security tools to check if your passwords and usernames have been leaked on the dark web.
In the event of a breach, change your passwords immediately to prevent further unauthorised access.
Avoid Password Reuse
There’s a common thread that runs through all of these hacking techniques:
Password reuse.
A recent survey from PCMag found that 70% of people use the same password for at least two accounts. Nearly 1 in 5 people use the same password for everything.

Hackers take advantage of password reuse to gain access to multiple accounts. A breach in one account can lead to a domino effect, compromising all other accounts.
It goes without saying you should be creating strong and unique passwords for each account you use. And you can consider the use of a password manager or a password book to reduce the need to memorise multiple passwords.
Protect Your Accounts with Strong Passwords
Understanding the techniques hackers use to steal passwords is an important first step to safeguarding your online identity.
Being aware of these threats and implementing robust security practices can significantly reduce the risk of falling victim to cybercriminals.

