Did you know around 140,000 UK businesses are using Microsoft Office 365?
The number of people using the software suite rose drastically over the course of the pandemic when the majority of the UK workforce became remote.
A large portion of Microsoft's success in 2020 can be attributed to its Teams app which attracted 95 million new users, one of the main selling points being its heavy integration with Microsoft 365.
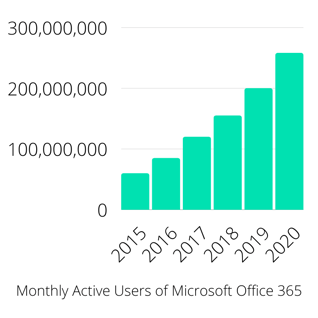
While Microsoft is clearly having no problem gaining 365 users, a significant barrier that is still preventing businesses from migrating to cloud-based services are the Office 365 security concerns.
Although Microsoft has its own built-in security, relying solely on your cloud provider to keep your business secure is not recommended.
As a business, it's still important to maintain visibility and control and, if necessary, implement third-party solutions to make sure you stay as secure as possible.
In this article, we'll take a look at the main security issues that businesses are concerned about when using Office 365 and how to tackle them effectively.
Top 4 Microsoft Office 365 Security Concerns
Want to skip ahead? This is what we'll be covering:
More of a visual learner? Jump straight to this infographic.Account Breaches
Of course, the worry we all start with is: How easily could a hacker break into my account?
If cybercriminals crack the code to gain access to a user's 365 account, they could expose your business' sensitive data and use their new identity to send out malicious emails to other employees at the company - or worse, your clients. This is a serious threat whatever size or sector your organisation.

Here's the deal:
Unfortunately, hackers are just getting smarter and smarter, so account breaches are never going to be 100% avoidable. But you don't have to make things easy for them...
Make sure you've got MFA
If you've ever been in conversation with any kind of security professional, you're probably not hearing this for the first time.
Multi-Factor Authentication involves a user having to provide multiple pieces of evidence of their identity before gaining access to, say, their 365 account.
This is a base-level security measure you can implement which will make it very challenging for a cybercriminal to break into your company's Office 365.
MFA should be set up for all user accounts, especially admin accounts - hackers normally go for these accounts because of their high-level access privileges.

Microsoft Office 365 security defaults require MFA for all accounts, but if you're on a business plan you can take an even more advanced approach using Conditional Access Policies.
As an admin, this will allow you to set policies and request additional actions when a user is signing in to access their account.
Use a strong password
Even after you've got MFA enabled, you need to make sure you've got a strong password.
The best kind of defence is a layered one, so a long non-guessable password is going to give you extra worthwhile protection; because nothing is totally hacker-proof.
Quick reminder: avoid using the same password everywhere and make sure you throw in some numbers and special characters.
Oh, and if you're forgetful like me, you may find a password manager helpful!

Are your employees cyber aware?
91% of cyber attacks start with a phishing email.
We all get busy during the working day, inboxes filling up, new emails coming in. You can imagine how easy it is to drop your guard and click on a link to a malicious website.
Human error remains the number one cause of cyber attacks so education remains the number one prevention tactic.

Ideally, you would invest in proper cyber security training for your staff but even if it's just sessions from your internal IT team or some useful resources that you circulate, any kind of cyber awareness training is better than none at all.
Make sure your employees are kept up to date on your security policies and are regularly informed on password and email security best practices.
Access Privileges
Another contributing factor to good Office 365 security is setting up access privileges correctly. Far too often, businesses can be very unrestrictive in terms of who can access what internally.
The general rule is anyone within your organisation should only be able to access that which they need to perform their job role and nothing more.
Giving excessive access to those in your business increases your risk of a data breach because if their account is hacked, the hacker may be able to access a vast amount, if not all, your sensitive data.
Microsoft 365 allows you to set certain users as admin roles. This is usually for the most senior members of your company and will grant them access to pretty much everything in your 365.
It's recommended that you have no more than 4 admins though, as obviously the more you have, the more risk of your data getting compromised.
Don't forget, when an employee leaves your organisation, you must remove ALL their access and delete their Office 365 account.
External threats are not the only threat out there and there have been quite a few tales of a disgruntled ex-employee causing issues. Just look at what happened to this IT Consulting Firm.
Data Loss and Leakage
Are you still with me?

This is probably the biggest security concern when it comes to using Cloud services like Microsoft Office 365.
Data protection is not only an important part of maintaining trusting relationships with customers, suppliers and stakeholders, but it's also a legal requirement, and you could suffer real consequences if you experience a breach because you've not taken the necessary steps to keep your data secure.
How might data be lost or compromised in my Office 365?
The two most common reasons for data loss within your 365 services are user error and cyber attack.
-
User Error
No one's perfect. Accidentally deleting data happens more frequently than you'd think. It could be an employee deleting a file they thought was no longer needed or simply clicking the wrong button by accident!
Similarly, someone may unintentionally overwrite some data. Although Microsoft offers version management, it can be problematic if you don't catch your mistake soon enough.
Integrating 3rd-party applications can also cause issues. If they've been poorly developed or contain bugs and have access to your data, something could get inadvertently deleted or tampered with.
-
Cyber Attack
The dreaded Cyber Attack...
If a hacker breaks into your account, they may be able to steal data or delete it. Another hacker trick is to encrypt your data with malware and demand a ransom to restore it.
Before you think about it, it's never recommended to actually pay the ransom...hackers aren't well known for playing fair!
.jpg?width=650&name=michael-geiger-JJPqavJBy_k-unsplash%20(1).jpg)
Having your data compromised in this way could affect your business' reputation, disrupt operations, and even have legal and financial repercussions.
Microsoft 365 does have anti-malware software but there's no guarantee it will detect and protect you from everything and many choose to implement further protective products and services which will defend their entire infrastructure including 365.
Backup, Backup, Backup!
How many times have you heard this? I'm guessing a few.
That's because this is the first way you're going to retrieve any data that you've lost, yet still, an impressive 30% of people have never backed up.
So how do you do it?

As a business, you need to identify the crucial data that has to be backed up. Think 'on a scale of 1-10 how bad would it be if I lost X data'. You can choose to back up with another cloud provider, or locally on an external hard drive or disk. You can also keep them off-site but make sure the data is encrypted for extra protection.
Whatever method you choose, your backups should be regularly monitored and it is recommended that you keep to a schedule so things are backed up often enough.
It's also a good idea to test your recovery speed. If you do lose data that affects business operations, how quickly can you recover that data from a backup?
Data Classification
Properly classifying your data and having a clear picture of where it is all stored, both in your internal and backup systems, will really help you keep it secure.
There will likely be different kinds of data that your business deals with, ranging from publicly accessible data all the way to highly sensitive personal data like payment information or health records.
Understand the importance of all the data. Ask yourself - What would be the consequences if this data got leaked, tampered with or deleted? Would you face regulatory fines? Incur revenue losses? Would it impact you operationally?
Managing your data well and controlling who has access to it will massively reduce your chances of it falling into the wrong hands.
Make use of Data Loss Prevention Tools
Microsoft 365 actually offers DLP to Office 365 E5 customers so you can monitor and protect your important data.
Data Loss prevention applies rules and policies to classify your data is and ultimately reduce the chance of losing it. If the rules are violated, you'll get alerted.
There are plenty of other DLP tools and providers out there too, so don't feel you have to stick with Microsoft.
Email Security
Email is critical to businesses operations and we can't do without it, so you want to know that whatever email service you're using is as secure as it can be.
With the popularity of Office 365, hackers know to target these users, with attacks like phishing, spam and ransomware. They will typically use email as an initial compromise to get in and if they are successful in gleaning credentials and breaching an account, they can scale up the breach and its impact.
We've all had suspicious emails appear in our inboxes. Some of these can be really obvious...
"You've won a new MacBook Pro, click the link to claim your prize"

Here's a quick reminder of what to look out for if you think you're being scammed:
1. Check the email domain 📩
Proper company emails will be sent from a company email address, not @yahoo or @gmail. Also, check it matches the name of the sender - if it does, it should be reliable.
Read it carefully as sometimes scammers will be sneaky and spell the company name ever so slightly differently!
2. Misspellings! 📖
Often, you can spot a scammer by poor spelling and grammar in the content of the email - think about it, a professional organisation wouldn't be letting badly typed emails go out to their customers!
3. Links 🔗
Scammers will often ask you to click on links but so might regular trustworthy emails you can trust.
Just make sure the URL looks legitimate and is in line with the company's website URL. Be extra careful with links and attachments as this is how scammers like to infect your systems with ransomware.
3. Content ✍️
Finally, just be sensible about the nature of the content. Are they asking for personal details or bank details? Trying to make things seem really urgent?
The scammer wants to panic you and make you think there's a chance you'll lose something if you don't ACT NOW.
But be smarter, take the time to run through these checks when you open an email you're unfamiliar with. You'll be grateful for it later!
Business Email Compromise
Others are harder to spot because they appear to be from a legitimate contact that you know.
You wouldn't immediately assume that anything was wrong but their email address could have been compromised.
Business email compromise is a big security concern for businesses.
If a hacker gets into your 365 account and accesses your email client, they may send emails disguised as you, which could lead to a number of consequences. Often high-level executives at a company or those involved in financial activities will be targeted in these attacks.
BEC could result in a very damaged business reputation as well as financial losses if the hacker has directly contacted suppliers, customers and partners. They may be gathering data or even intercepting invoices to redirect payments into their own bank accounts.

It's always best to be sceptical of any email you get and keep in mind the spam warning signs.
Office 365 Email Security
Microsoft 365 has a good selection of integrated security features designed to deal with email threats, including malware protection and email encryption.
Advanced features in 365 business plans also include Microsoft Defender which scans emails and links to protect against phishing and other cyber attacks.
Seeking out more advanced solutions to supplement Office 365's security is a popular option for businesses, whatever size you are.
Office 365 email security is a good start but other tools will allow you to have more control and visibility over activity in your business' outlook and the rest of your 365 tenant, detecting and alerting you of threats right away.
💡Bonus Tip💡 Often, if a hacker breaks into your Office 365, they'll change your inbox rules so messages sent from the user get deleted or forwarded and they can go undetected as they wreak havoc on your systems! Remember to adjust your alerts policies and set some alerts to help you monitor such activities.
Best Practices to Keep Your Office 365 Secure
As you've seen, Microsoft has done a good job at providing security features within 365 that can help your business stay protected, but no solution is 100% effective.
Depending on your Microsoft 365 subscription, there are measures you can implement to improve your security from the inside.
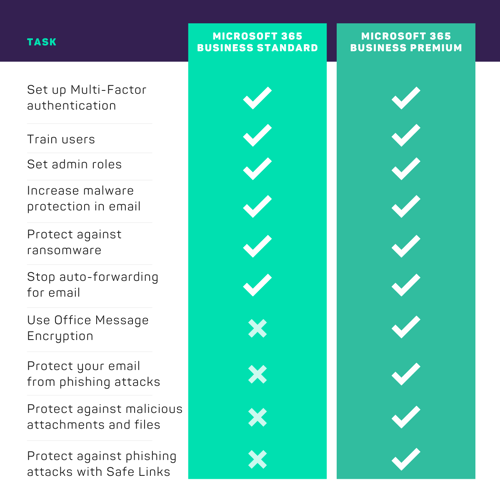
Head to Microsoft 365 Security and Compliance Center for more information.
For some organisations, the existing security features will be enough, but a layered defence is always the best one, so consider creating an even more secure environment with third-party tools and services designed to help keep your 365 secure.
Employee Awareness
Don't forget - human error is still the number one cause of attacks. Whether it's an accidental deletion of data, clicking on a suspicious email link or opting for a password like 'password123', these are things that can be avoided by ensuring your workforce are informed and aware of cyber threats and how to be cyber secure.
Keep employees up to date with your business' security policies and processes regarding Office 365 so they are best equipped to deal with security risks and they can avoid being one themselves!
Conclusion
If Office 365's growth in the last few years is anything to go by, it's quite safe to say that the software suite will continue to attract businesses and individuals as an easily accessible collaborative environment for work.
People will continue to be apprehensive about Cloud services and security concerns are likely to remain the primary reason for this, but hopefully this article has shed some light on the security measures that are available in 365 and what solutions you can explore in addition to this.
For a quick overview of the top 4 Office 365 security concerns listed here, take a look at the infographic below.
.png?width=650&name=140%2c000%20(1).png)


