Hackers know you're at home and they know your network is vulnerable...
With the UK Government putting pressure on businesses to promote social distancing to avoid the spread of COVID-19, we've all been put in avery unique situation.
We're working from home and for many of us, this is the first time we've had to do this.
Before COVID-19, we had comfort and peace of mind as we knew our specialised staff, behind the scenes, would constantly be protecting our businesses from cyber attacks.
Suddenly, that comfort and peace of mind has gone.
No one is with you in your home protecting you, no one is coming to your house to secure your network.
So it is now the time to go DIY and do it ourselves.
If you can protect yourself, you can protect your business and that goes for every member of staff in your organisation too.
Following the tips in this article will reduce your risk of being breached immensely, the last thing your organisation needs in these uncertain time is a loss of data.

What are the 11 things you should right now to improve your remote cyber security?
1. Change and create strong passwords
If your password is your wife's name, we've got big issues we need to fix!
Here's what you need to do right now:
- Get yourself a password manager, I recommend using Dashlane. Many people will use the same password for every website, the problem with this is once a hacker has one account, he has potentially every account you've ever created.
With a password manager, you can keep track of every password and make sure they're as secure as possible without having to worry about remembering them. - Following on from the last step, create a new password for each website you spend a significant amount of time on. This should range from email, social media, company portals, absolutely everything. Remember, you wouldn't change your socks every 5 years... change your passwords frequently!
- Make sure to use minimum of 12 characters, special characters and make it as complex as possible. Don't worry about remembering it, that's why you're using a password manager. This is simply about securing yourself as much as possible, steer clear of things someone could directly relate to you (E.g. your name, location or interests).
2. Use a reliable Virtual Private Network (VPN)
NordVPN are one of the best and most reliable VPN services out there and they define a VPN as "a service that encrypts your Internet traffic and protects your online identity".
You don't want to be watched or tracked whilst accessing sensitive data, this is why it is incredibly important to use a VPN as they will encrypt your communications and hide your I.P address.
VPNs can be quite expensive, I recommend looking for a multi-year deal for when you do purchase one, ask your company if they've currently got a subscription too as this would save you some money. Steer clear of free VPNs!
3. Use a reliable Anti-Virus software
Anti-Virus software are a staple of individual security, it's crucial to have the software set up on your device to prevent Trojans, Malware and Viruses destroying your device.
When it comes to Anti-Virus, I'd recommend pursuing the McAfee Anti-Virus Suite or the Norton Anti-Virus suite, they will both do an incredible job.

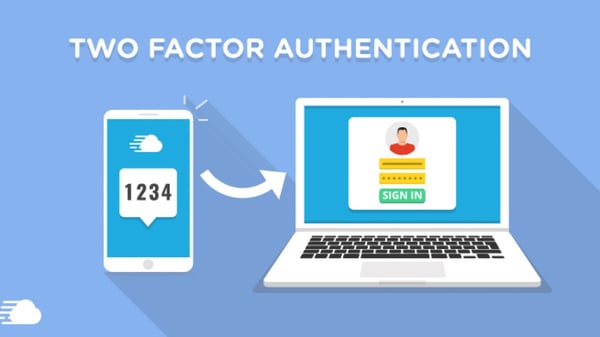
4. Enable Two Factor Authentication
Two-factor authentication (2FA) is a simple way to add an extra layer of security to your accounts. The most common 2FA method used by popular online services is a text message with an authentication code sent to your phone.
Make sure you've got 2FA enabled across all your most frequently used websites so hackers have to go an extra step.
Another great thing about 2FA is if someone does try to access your account, you have time to go and change your passwords as you would have seen the email/text pop up on your device.
5. Get suspicious
You know those poorly written emails telling you that you've got £5000 back from HMRC? Yes, those are Phishing emails and we've all seen one before.
This is the exact type of tactic cyber criminals are using to get your sensitive data.
I'm sure you're aware of how opportunistic hackers and cyber criminals are. They will be using this pandemic against you, trying to trick you into doing something you usually you wouldn't do so it can benefit them.
For instance, take a look at the following three emails (via the U.S. Health and Human Services website)
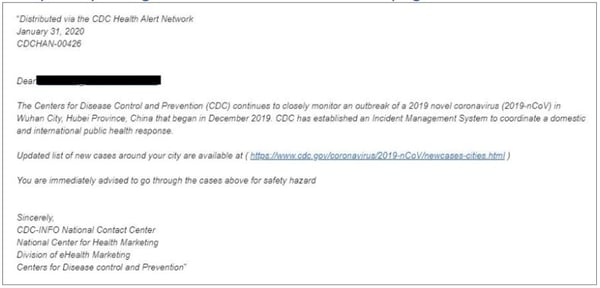
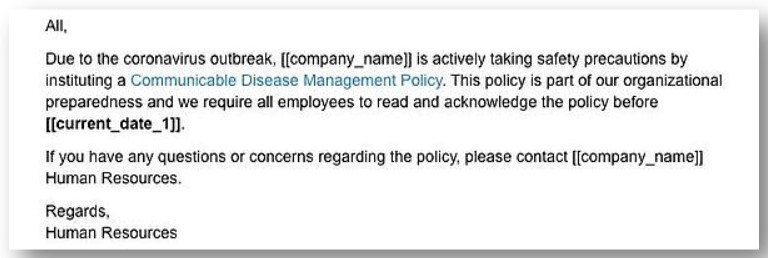
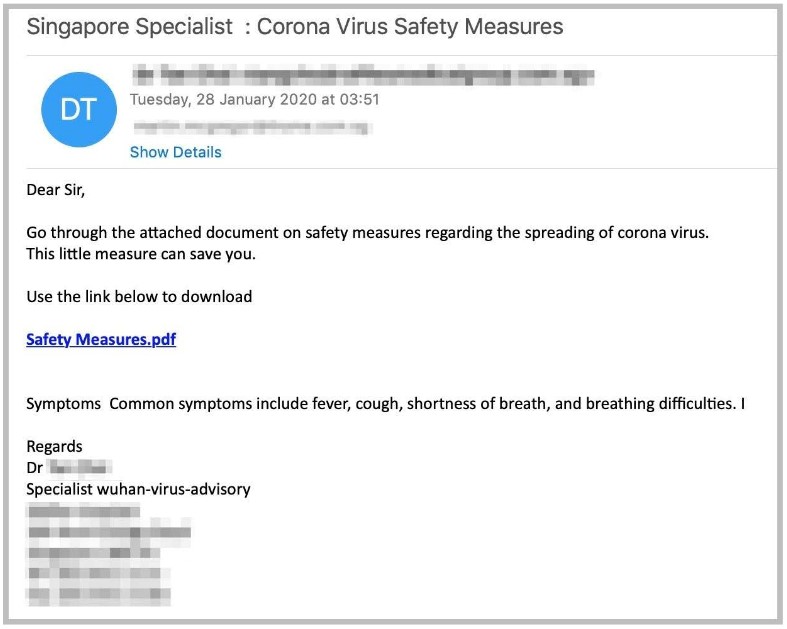
These are just three examples of cyber criminals using COVID-19 in order to profit.
It's really important that you're able to spot a Phishing email from a normal one so here's nine things you should do when you receive an email:
- Look but don't click, you need to properly dissect the email to understand if it is real or not.
- Don't trust the display name of the email, it may say 'HSBC' but the email address may say 'anonymous@hotmail.co.uk'
- Check for spelling errors, these are very prevalent in Phishing emails but remember to be wary as Phishing emails are getting more and more clever.
- Is the email asking for personal information? It is very unlikely you'd ever get asked for personal information over email
- Does it just sound 'off' to you? It most likely is a Phishing email.
- Is the email pushing urgency? Phishing emails notoriously pressure you into doing something, don't fall for the pressure.
- Check the email signature, most legitimate senders will include one.
- Do not click attachments, you don't want to accidentally download software which exposes every document on your device.
- Don't believe everything you see.
6. Avoid Public Wi-Fi
If you do end up in a situation where you have Public Wi-Fi available, I would recommend staying away from it. Public Wi-Fi is a notorious trap used by hackers all around the world, it's certainly not worth losing your company's valuable personal and sensitive data for.
However, if it is absolutely urgent, your task should be quick and the secure VPN I mentioned earlier should be used throughout all your tasks.

7. Put up your firewall
Enabling your firewall (Every device should have one) will mean you block certain transmissions on your device. Most will have this on as a default option but if not, make sure to enable it. A quick google search should give you the instructions you need to enable it for your particular device.
8. Protect and secure your broadband router
Chances are, your house is using WiFi from a broadband router and the way these routers are not as secure as they could be. Here's what you can do to secure to them:
- Using tips I gave earlier about passwords, create a complicated password and remember to change it frequently
- Change the router's admin settings by creating a strong and complicated admin password
- Change your SSID (Router's Name) to something bland, don't encourage hackers by trying to be too clever with it.
- Strengthen the encryption on your router by switching to WPA2 AES.
- Turn on the router firewall
- Make sure to update your router's software as frequently as possible
9. Choose a backup solution
Data might just be the life blood of your organisation, without it, you're in serious trouble. I highly recommend backing up your data, make sure to:
- Implement a hybrid backup which consists of a physical backup device (such as a hard drive) as well as an intangible back up solution (such as cloud storage). If this seems quite daunting, have a look at ZDNet's article on deciding which back up solution would be best for your business
- Opt for a daily backup if you have the capacity. However, if this is unrealistic, you can opt for a weekly or monthly backup instead.
![]()
10. Remove and Update Applications
There are number of applications on your devices which can get exhausted after a certain period of time and people remain unaware of it. These applications and services act as loopholes for your system's security.
You need to delete that particular application and the user credentials associated with it to prevent hackers from taking any sensitive data. You want to do this across all your devices and if you see an application you don't remember downloading, delete it promptly.
Also, make sure your software is being automatically updated as developers are constantly finding solutions to security gaps in their applications.

11. Encrypt, Encrypt, Encrypt
Every communication channel you use will need to be encrypted, whether that is the email on your PC or instant messaging on your phone. I recommend using Whatsapp with colleagues as this is already set up with default encryption and when using a PC, I recommend using Microsoft Teams as this has a very advanced set of security controls in place to prevent your data being stolen.

12. BONUS TIP! Demonstrate Homeworkers Security by achieving Cyber Essentials Plus
Well, these are absolutely valid questions if you're asking a regular certification body. However, Cyber Tec Security are an IASME Certification body and we can:
Download your FREE copy of The Ultimate Guide to Cyber Essentials Now!